The Microsoft Intune admin center (https://endpoint.microsoft.com) has a lot of great features to view and manage applications and devices. However, understanding which policies and applications are assigned with which Azure Active Directory (AAD) groups requires multiple steps.
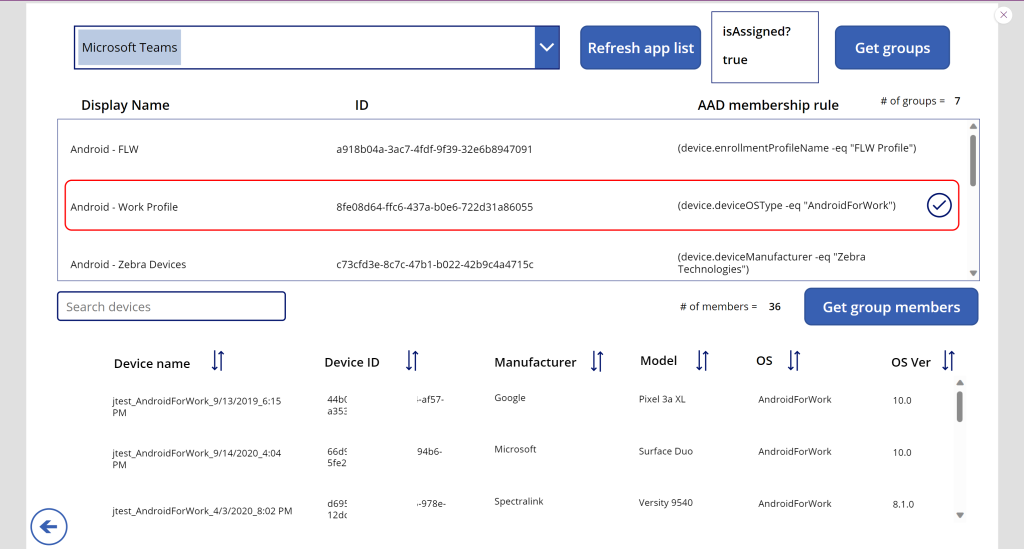
For example, if we want to view which groups are assigned to the Microsoft Teams app for Android, we need to search for and select the app, select properties, and view the assigned groups. Assignments only shows the admin which AAD groups are assigned, not the members of the group. This is ok for when there aren’t many apps or policies or group assignments, however my Intune tenant has nearly 500 applications across all platforms and when troubleshooting, clicking in and out of screens can be repetitive and time consuming.
To improve troubleshooting and to reduce the number of steps, I created a Power App that pulls in all policies and applications to a Power App. When an app or policy is selected, the app will show all the associated AAD groups and as a bonus will display all the members of a selected group.
I can tell you that by creating this Power App I have found a few issues with group assignments in my own tenant and I’m meticulous about policy and app assignments (naming my policies could be improved though :)).
Below is a screenshot of members of a selected AAD group for a selected configuration policy:
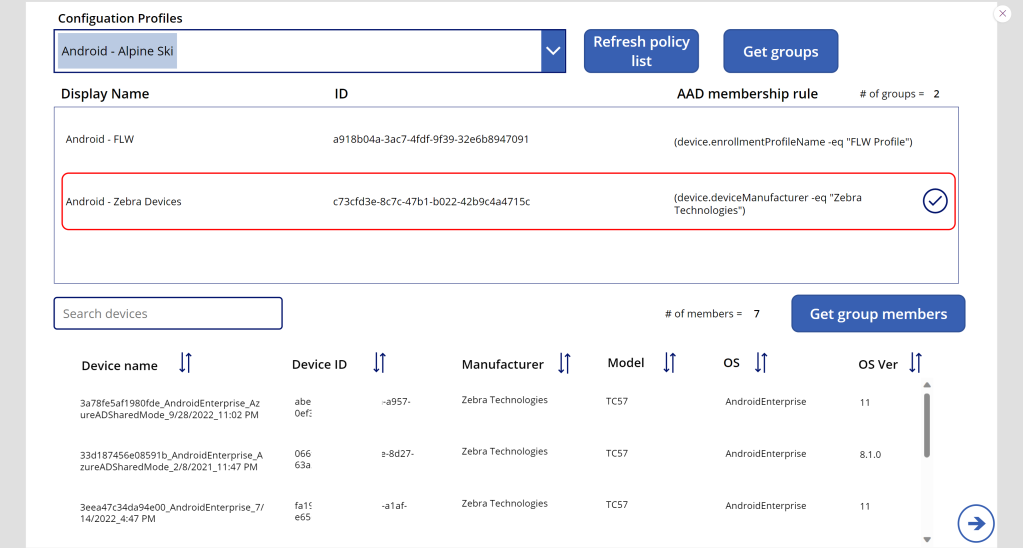
Note: Device IDs are blurred out
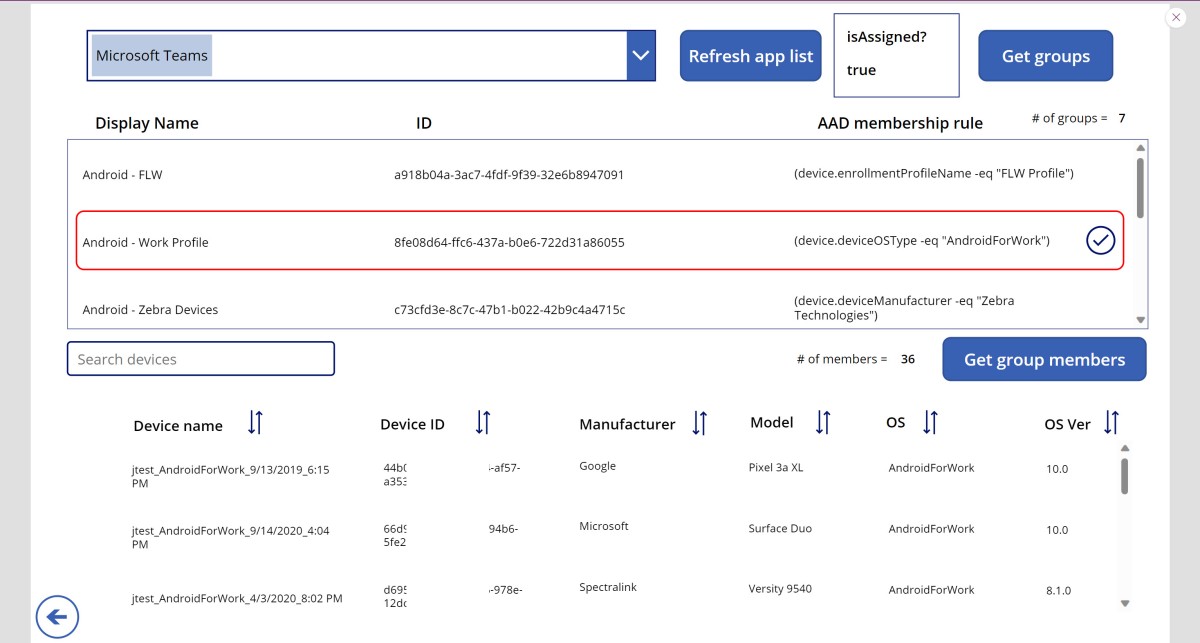
Below is a screenshot of members of a selected AAD group for a selected application:
Note: Device IDs are blurred out
Let’s get started!
Requirements:
- Microsoft Intune
- Microsoft Graph
- Power Automate
- Power Apps
For this post I’m doing something different by simplifying the content and sharing the entire solution, scrubbed of sensitive information, with you. Since I rarely share apps, I make no claims or guarantees about importing or execution or security. Feel free to download the app from GitHub, look through each file and all the JSON to understand what the app and Flows are doing.
Why am I sharing the entire app? This is a fairly large app with two screens and six Flows and many of my previous blogs can be utilized to piece this solution together. So for the sake of time and convenance to you, I’m sharing out the entire app.
Navigate to Power Apps and select Apps > Import canvas app. After import, you’ll need to update the Tenant ID and three variables in each of the six Power Automate Flows:
- Tenant name marked with “YOURTENANT.onmicrosoft.com”
- AAD registered App client ID marked with “AADRegistedAppClientID”
- AAD registered App secret marked with “YourAADRegisteredAppSecret”
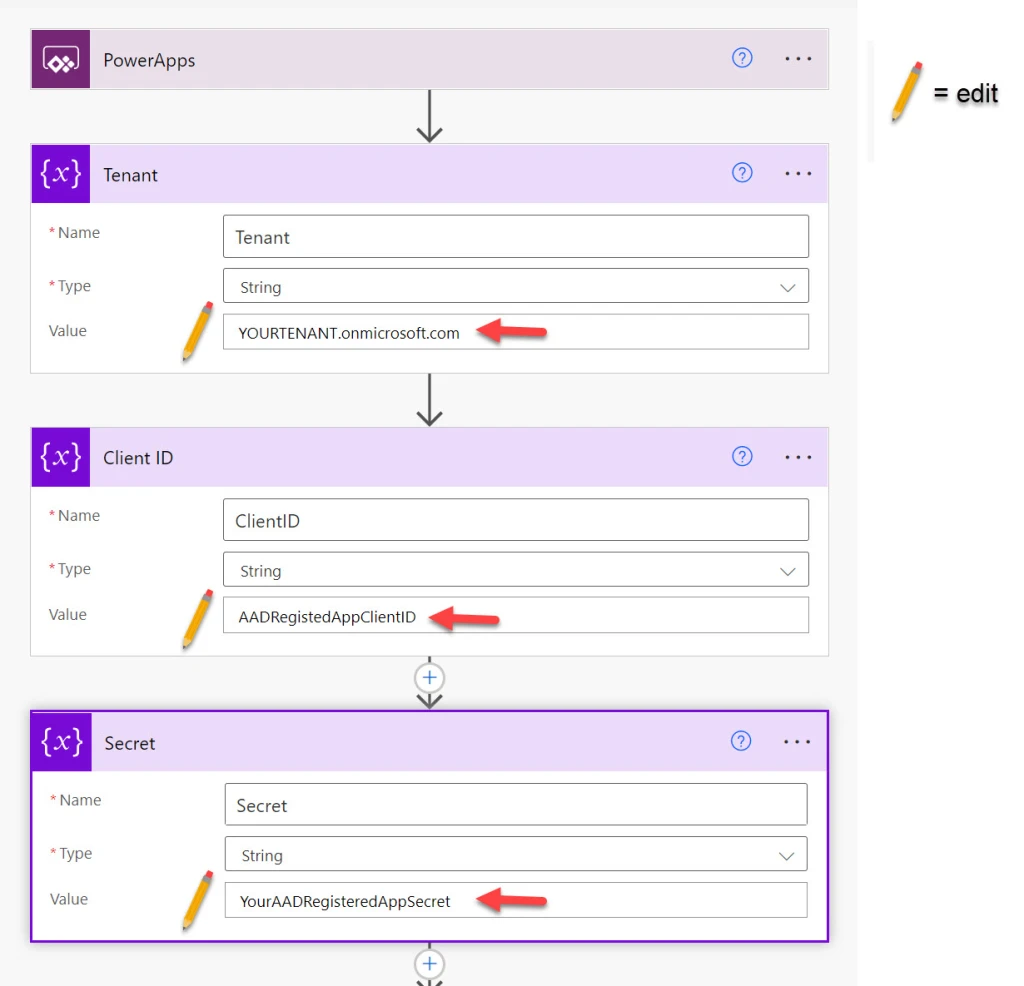
Note: in previous posts I embedded the tenant name, AAD clientID, and AAD secret in the HTTP get action. Breaking out to variables allows for centralized management of these attributes, however the HTTP get action still requires those attributes be filled in with the new variables.
Download the full Power App from GitHub:
https://github.com/courtenaybernier/Power-Apps-AAD-group-assignments-in-IntuneConclusion
I hope you’ll find this useful and maybe expand on what I’ve designed here. Again, I make no claims or guarantees about importing or execution or security, utilize at your own risk. Look through all the JSON files to see what the app is doing and move forward how you desire.